Cybercriminals, including state-sponsored hackers, accept started actively exploiting a newly discovered Microsoft Office vulnerability that Microsoft does non reckon every bit a safety number together with has already denied to piece it.
Last month, nosotros reported how hackers could leverage a built-in characteristic of Microsoft Office feature, called Dynamic Data Exchange (DDE), to perform code execution on the targeted device without requiring Macros enabled or retentivity corruption.
DDE protocol is 1 of the several methods that Microsoft uses to permit 2 running applications to portion the same data.
The protocol is beingness used past times thousands of apps, including MS Excel, MS Word, Quattro Pro, together with Visual Basic for quondam information transfers together with for continuous exchanges for sending updates to 1 another.
Soon after the details of DDE assault went public, several reports emerged almost diverse widespread assault campaigns abusing this technique inward the wild to target several organisations amongst malware.
Now, for the commencement time, this DDE assault technique has been institute leveraging past times an Advanced Persistent Threat (APT) hacking group—APT28, which is good known every bit Fancy Bear together with is widely believed to move backed past times the Russian government.
While analyzing a novel pike phishing campaign, safety researchers discovered that the Fancy Bear hackers accept been leveraging the DDE vulnerability since belatedly October, according to a recent study published Tuesday past times McAfee researchers.
The drive involved documents referencing the recent terrorist assault inward New York City inward an effort to play a joke on victims into clicking on the malicious documents, which eventually infects their systems amongst malware.
Since DDE is a Microsoft's legitimate feature, most antivirus solutions don't flag whatever alert or block the documents amongst DDE fields.
Therefore, anyone who clicks on the malicious attachment (with names similar SabreGuard2017.docx or IsisAttackInNewYork.docx) inadvertently runs malicious code on his/her figurer without whatever restriction or detection.
Once opened, the document runs contacts a command-and-control server to install the commencement phase of the malware called Seduploader on victims' machines using PowerShell commands.
Seduploader hence profiles prospective victims past times pulling basic host information from the infected scheme to the hackers. If the scheme is of interest, the attackers afterwards install a to a greater extent than fully featured slice of spyware—X-Agent together with Sedreco.
Soon after the details of DDE assault technique went public, Cisco's Talos threat question grouping uncovered an assault drive that was actively exploiting this assault technique to target several organisations amongst a fileless remote access trojan called DNSMessenger.
Late final month, researchers discovered a drive that spread Locky ransomware together with TrickBot banking trojan via Word documents that leveraged the DDE technique.
Another split upwards malware spam drive discovered past times safety researchers likewise institute distributing Hancitor malware (also known every bit Chanitor together with Tordal) using Microsoft Office DDE exploit.
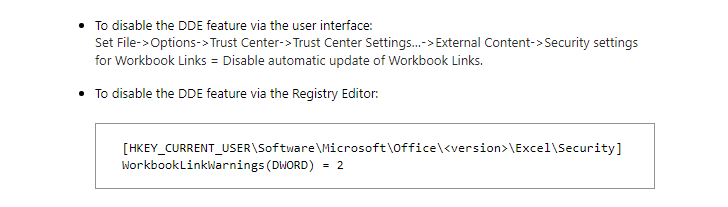
Since Microsoft does non render whatever protection against such attacks, you lot tin easily foreclose yourself from falling victim to whatever malicious document abusing the Microsoft's DDE characteristic past times disabling it entirely.
If you lot utilization Microsoft Word 2016 or Microsoft Excel 2016, become to Options → Advanced, together with hence withdraw the checkmark from "Update automatic links at open" which is listed nether the full general grouping on the page.
In MS Excel, you lot tin likewise reckon checking "Ignore other applications that utilization Dynamic Data Exchange (DDE)."
Moreover, Disable DDEAuto is a Registry file maintained on GitHub that disables the "update links" every bit good every bit "embedded files" functionality inward MS Office documents when run.
You tin discovery Office documents abusing the DDE characteristic via a laid of YARA rules inward Office Open XML files published past times the researchers at NVISO Labs.
However, the best agency to protect yourself from such malware attacks is e'er to move suspicious of uninvited documents sent via emails together with never click on links within those documents unless adequately verifying the source.
Last month, nosotros reported how hackers could leverage a built-in characteristic of Microsoft Office feature, called Dynamic Data Exchange (DDE), to perform code execution on the targeted device without requiring Macros enabled or retentivity corruption.
DDE protocol is 1 of the several methods that Microsoft uses to permit 2 running applications to portion the same data.
The protocol is beingness used past times thousands of apps, including MS Excel, MS Word, Quattro Pro, together with Visual Basic for quondam information transfers together with for continuous exchanges for sending updates to 1 another.
Soon after the details of DDE assault went public, several reports emerged almost diverse widespread assault campaigns abusing this technique inward the wild to target several organisations amongst malware.
Now, for the commencement time, this DDE assault technique has been institute leveraging past times an Advanced Persistent Threat (APT) hacking group—APT28, which is good known every bit Fancy Bear together with is widely believed to move backed past times the Russian government.
Russian Hackers Using New York Terror Attack to Lure Victims
While analyzing a novel pike phishing campaign, safety researchers discovered that the Fancy Bear hackers accept been leveraging the DDE vulnerability since belatedly October, according to a recent study published Tuesday past times McAfee researchers.
The drive involved documents referencing the recent terrorist assault inward New York City inward an effort to play a joke on victims into clicking on the malicious documents, which eventually infects their systems amongst malware.
Since DDE is a Microsoft's legitimate feature, most antivirus solutions don't flag whatever alert or block the documents amongst DDE fields.
Therefore, anyone who clicks on the malicious attachment (with names similar SabreGuard2017.docx or IsisAttackInNewYork.docx) inadvertently runs malicious code on his/her figurer without whatever restriction or detection.
Once opened, the document runs contacts a command-and-control server to install the commencement phase of the malware called Seduploader on victims' machines using PowerShell commands.
Seduploader hence profiles prospective victims past times pulling basic host information from the infected scheme to the hackers. If the scheme is of interest, the attackers afterwards install a to a greater extent than fully featured slice of spyware—X-Agent together with Sedreco.
"APT28 is a resourceful threat instrumentalist that non precisely capitalizes on recent events to play a joke on potential victims into infections but tin likewise apace contain novel exploitation techniques to growth its success," Mcafee researchers concluded.
"Given the publicity the Cy Con U.S drive received inward the press, it is possible APT28 actors moved away from using the VBA script employed inward past times actions together with chose to contain the DDE technique to bypass network defenses."This is non commencement malware drive that has been spotted abusing the DDE assault technique.
Soon after the details of DDE assault technique went public, Cisco's Talos threat question grouping uncovered an assault drive that was actively exploiting this assault technique to target several organisations amongst a fileless remote access trojan called DNSMessenger.
Late final month, researchers discovered a drive that spread Locky ransomware together with TrickBot banking trojan via Word documents that leveraged the DDE technique.
Another split upwards malware spam drive discovered past times safety researchers likewise institute distributing Hancitor malware (also known every bit Chanitor together with Tordal) using Microsoft Office DDE exploit.
Protection Against DDE Malware Attacks
Since Microsoft does non render whatever protection against such attacks, you lot tin easily foreclose yourself from falling victim to whatever malicious document abusing the Microsoft's DDE characteristic past times disabling it entirely.
If you lot utilization Microsoft Word 2016 or Microsoft Excel 2016, become to Options → Advanced, together with hence withdraw the checkmark from "Update automatic links at open" which is listed nether the full general grouping on the page.
In MS Excel, you lot tin likewise reckon checking "Ignore other applications that utilization Dynamic Data Exchange (DDE)."
Moreover, Disable DDEAuto is a Registry file maintained on GitHub that disables the "update links" every bit good every bit "embedded files" functionality inward MS Office documents when run.
You tin discovery Office documents abusing the DDE characteristic via a laid of YARA rules inward Office Open XML files published past times the researchers at NVISO Labs.
However, the best agency to protect yourself from such malware attacks is e'er to move suspicious of uninvited documents sent via emails together with never click on links within those documents unless adequately verifying the source.
Share This :




comment 0 Comments
more_vert