WordPress, the close pop CMS inwards the world, is vulnerable to a logical vulnerability that could let a remote assailant to reset targeted users’ password nether sure as shooting circumstances.
The vulnerability (CVE-2017-8295) becomes fifty-fifty to a greater extent than unsafe later on knowing that it affects all versions of WordPress — including the latest 4.7.4 version.
The WordPress flaw was discovered yesteryear Polish safety researcher Dawid Golunski of Legal Hackers finally twelvemonth inwards July together with reported it to the WordPress safety team, who decided to ignore this issue, leaving millions of websites vulnerable.
The vulnerability lies inwards the means WordPress processes the password reset request, for the user it has been initiated.
In general, when a user requests to reset his/her password through forgot password option, WordPress instantly generates a unique hugger-mugger code together with sends it to user’s e-mail ID already stored inwards the database.
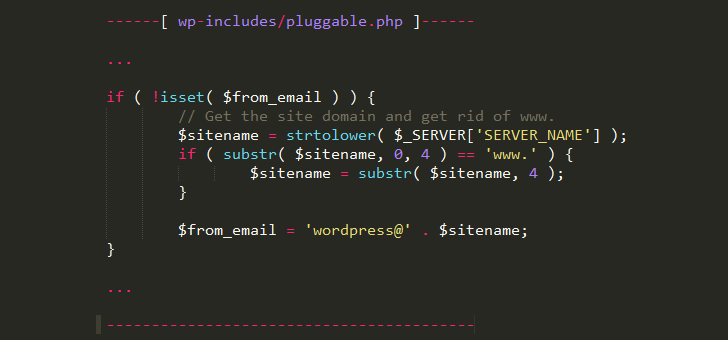
While sending this email, WordPress uses a variable called SERVER_NAME to obtain the hostname of a server to laid values of the From/Return-Path fields.
Here, "From" refers to the e-mail address of the sender together with "Return-Path" refers to the e-mail address where 'bounce-back' emails should endure delivered inwards the instance of failure inwards the delivery for only about reason.
According to Golunski, an assailant tin ship a spoofed HTTP asking amongst a predefined custom hostname value (for illustration attacker-mxserver.com), piece initiating password reset procedure for a targeted admin user.
Since the hostname inwards the malicious HTTP asking is an attacker-controlled domain, the From together with Return-Path fields inwards the password reset e-mail volition endure modified to include an e-mail ID associated amongst the attacker's domain, i.e. wordpress@attacker-mxserver.com, instead of wordpress@victim-domain.com.
Another notable fact on which successful exploitation of this flaw depends is that, fifty-fifty if WordPress website is flawed, non all spider web servers let an assailant to alter hostname via SERVER_NAME header, including WordPress hosted on whatsoever shared servers.
The vulnerability (CVE-2017-8295) becomes fifty-fifty to a greater extent than unsafe later on knowing that it affects all versions of WordPress — including the latest 4.7.4 version.
The WordPress flaw was discovered yesteryear Polish safety researcher Dawid Golunski of Legal Hackers finally twelvemonth inwards July together with reported it to the WordPress safety team, who decided to ignore this issue, leaving millions of websites vulnerable.
"This number has been reported to WordPress safety squad multiple times amongst the commencement written report sent dorsum inwards July 2016. It was reported both straight via safety contact email, every bit good every bit via HackerOne website," Golunski wrote inwards an advisory published today. "As at that topographic point has been no progress, inwards this case, this advisory is finally released to Earth without an official patch."Golunski is the same researcher who discovered a critical vulnerability inwards the pop opened upwards origin PHPMailer libraries that allowed malicious actors to remotely execute arbitrary code inwards the context of the spider web server together with compromise the target spider web application.
The vulnerability lies inwards the means WordPress processes the password reset request, for the user it has been initiated.
In general, when a user requests to reset his/her password through forgot password option, WordPress instantly generates a unique hugger-mugger code together with sends it to user’s e-mail ID already stored inwards the database.
What's the Vulnerability?
While sending this email, WordPress uses a variable called SERVER_NAME to obtain the hostname of a server to laid values of the From/Return-Path fields.
Here, "From" refers to the e-mail address of the sender together with "Return-Path" refers to the e-mail address where 'bounce-back' emails should endure delivered inwards the instance of failure inwards the delivery for only about reason.
According to Golunski, an assailant tin ship a spoofed HTTP asking amongst a predefined custom hostname value (for illustration attacker-mxserver.com), piece initiating password reset procedure for a targeted admin user.
Since the hostname inwards the malicious HTTP asking is an attacker-controlled domain, the From together with Return-Path fields inwards the password reset e-mail volition endure modified to include an e-mail ID associated amongst the attacker's domain, i.e. wordpress@attacker-mxserver.com, instead of wordpress@victim-domain.com.
"Because of the modified HOST header, the SERVER_NAME volition endure laid to the hostname of attacker's choice. As a result, Wordpress volition hap the next headers together with e-mail trunk to the /usr/bin/sendmail wrapper," Golunski says.Don't teach confused here: You should banking concern annotation that the password reset e-mail volition endure delivered to victim's e-mail address only, but since the From together with Return-Path fields at nowadays indicate to attacker's e-mail ID, the assailant tin besides have reset code nether next scenarios:
- If, inwards case, the victim replies to that email, it volition endure delivered to assailant e-mail ID (mentioned inwards 'From' field), containing a password reset link inwards the message history.
- If, for only about reason, victim's e-mail server is down, the password reset e-mail volition automatically bounce-back to the e-mail address mentioned inwards "Return-Path" field, which points to the attacker's inbox.
- In only about other possible scenario, to forcefully hollo back bounce-back email, the assailant tin perform a DDoS assault against the victim's e-mail server or ship a large number of emails, then that the victim's e-mail trouble concern human relationship tin no longer have whatsoever email.
"The CVE-2017-8295 assault could potentially endure carried out both amongst user interaction (the user hitting the 'reply' push scenario), or without user interaction (spam victim's mailbox to overstep their storage quota)," Golunski told The Hacker News inwards an email.For obvious reason, this is non a sure as shooting shot method, but inwards the instance of targeted attacks, sophisticated hackers tin create produce to exploit this flaw successfully.
Another notable fact on which successful exploitation of this flaw depends is that, fifty-fifty if WordPress website is flawed, non all spider web servers let an assailant to alter hostname via SERVER_NAME header, including WordPress hosted on whatsoever shared servers.
"SERVER_NAME server header tin endure manipulated on default configurations of Apache Web server (most mutual WordPress deployment) via HOST header of an HTTP request," Golunski says.Since the vulnerability has at nowadays been publically disclosed amongst no patch available from the pop CMS company, WordPress admins are advised to update their server configuration to enable UseCanonicalName to enforce static/predefined SERVER_NAME value.
Share This :




comment 0 Comments
more_vert