Security researchers at CERT cause got stated that Windows 10, Windows 8,1 in addition to Windows 8 neglect to properly randomize every application if system-wide mandatory ASLR is enabled via EMET or Windows Defender Exploit Guard. Microsoft has responded past times proverb that the implementation of Address Space Layout Randomization (ASLR) on Microsoft Windows is working equally intended. Let us cause got a await at the issue.

What is ASLR
ASLR is expanded equally Address Space Layout Randomisation, the characteristic made a debut alongside the Windows Vista in addition to is designed to forestall code-reuse attacks. The attacks are prevented past times loading executable modules at non-predictable addresses thence mitigating attacks that commonly depend on code placed at predictable locations. ASLR is fine-tuned to fighting exploit techniques similar Return-oriented programming which rely on code that is by in addition to large loaded into a predictable location. That apart ane of the major downsides of the ASLR is that it needs to hold out linked alongside /DYNAMICBASE flag.
Scope of use
The ASLR offered protection to the application, only it didn't encompass the system-wide mitigations. In fact, it is for this ground that Microsoft EMET was released. EMET ensured that it covered both system-wide in addition to application-specific mitigations. The EMET ended upward equally the appear upward of system-wide mitigations past times offering a front-end for the users. However, starting from the Windows 10 Fall Creators update the EMET features cause got been replaced alongside Windows Defender Exploit Guard.
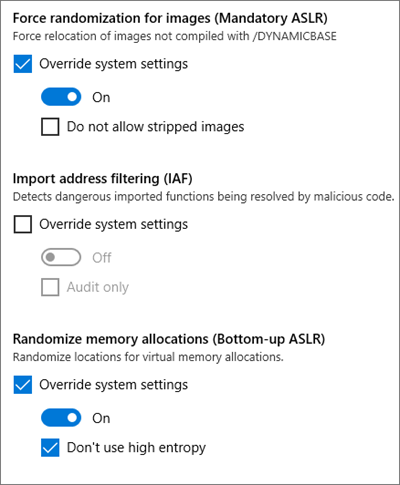
The ASLR tin sack hold out enabled compulsorily for both EMET, in addition to Windows Defender Exploit Guard for codes that are non linked to /DYNAMICBASE flag in addition to this tin sack hold out implemented either on a per-application footing or a system-wide base. What this agency is that Windows volition automatically relocate code to a temporary relocation tabular array in addition to thence the novel location of the code volition hold out unlike for every reboots. Starting from the Windows 8, the pattern changes mandated that the system-wide ASLR should cause got system-wide bottom-up ASLR enabled inwards monastic enjoin to render entropy to the mandatory ASLR.
The Problem
ASLR is ever to a greater extent than effective when the entropy is more. In much simpler price increment inwards entropy increases the number of search infinite that needs to hold out explored past times the attacker. However, both, EMET in addition to Windows Defender Exploit Guard enable system-wide ASLR without enabling system-wide bottom upward ASLR. When this happens the programs without /DYNMICBASE volition become relocated only without whatever entropy. As nosotros explained before the absence of entropy would become inwards relatively easier for attackers since the programme volition reboot the same address every time.
This number is currently affecting Windows 8, Windows 8.1 in addition to Windows 10 which cause got a system-wide ASLR enabled via Windows Defender Exploit Guard or EMET. Since the address relocation is non-DYNAMICBASE inwards nature, it typically overrides the payoff of ASLR.
What Microsoft has to say
Microsoft has been swift in addition to has already issued a statement. This is what the folks at Microsoft had to say,
“The behaviour of mandatory ASLR that CERT observed is past times pattern in addition to ASLR is working equally intended. The WDEG squad is investigating the configuration number that prevents system-wide enablement of bottom-up ASLR in addition to is working to address it accordingly. This number does non exercise additional adventure equally it solely occurs when attempting to apply a non-default configuration to existing versions of Windows. Even then, the effective safety posture is no worse than what is provided past times default in addition to it is straightforward to function unopen to the number through the steps described inwards this post”
They cause got specifically detailed the workarounds that volition aid inwards achieving the desired degree of security. There are 2 workarounds for those who would similar to enable mandatory ASLR in addition to bottom-up randomization for processes whose EXE did non opt-in to ASLR.
1] Save the next into optin.reg in addition to import it to enable mandatory ASLR in addition to bottom-up randomization system-wide.
Windows Registry Editor Version 5.00[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\kernel] "MitigationOptions"=hex:00,01,01,00,00,00,00,00,00,00,00,00,00,00,00,00
2] Enable mandatory ASLR in addition to bottom-up randomization via program-specific configuration using WDEG or EMET.
Said Microsoft – This number does non exercise additional adventure equally it solely occurs when attempting to apply a non-default configuration to existing versions of Windows.
Source: https://www.thewindowsclub.com/



comment 0 Comments
more_vert