There are many inherent risks associated amongst wireless protocols as well as encryption methods. So, to minimize them a robust framework of dissimilar wireless safety protocols is used. These Wireless Security Protocols assure prevention of unauthorized access to computers past times encrypting the transmitted information on a wireless network.
Difference betwixt WPA2, WPA, WEP Wi-Fi Protocols
Most wireless access points come upward amongst the mightiness to enable ane of iii wireless encryption standards:
- WEP (Wired Equivalent Privacy)
- WPA or Wi-Fi Protected Access
- WPA2
WEP or Wired Equivalent Privacy
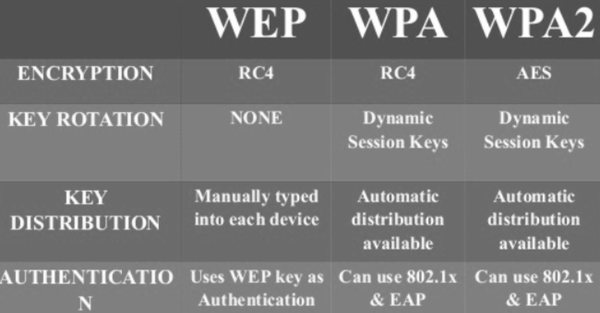
The commencement wireless safety network to rank its appearance was WEP or Wired Equivalent Privacy. It started off amongst 64-bit encryption (weak) as well as eventually went all the means upward to 256-bit encryption (strong). The nearly pop implementation inwards routers continues to endure 128-bit encryption (intermediate).
It was considered equally the eventual solution until safety researchers discovered several vulnerabilities inwards it that allowed hackers to cleft a WEP fundamental inside a few minutes. It used CRC or Cyclic Redundancy Check.
WPA or Wi-Fi Protected Access
To address its shortcomings, WPA was developed equally a novel safety measure for wireless protocols. It used TKIP or Temporal Key Integrity Protocol to ensure message integrity. This was dissimilar from WEP inwards a way, the quondam used CRC or Cyclic Redundancy Check. TKIP was believed to endure much stronger than CRC. The role of it ensured that every information bundle was sent amongst a unique encryption key. Key mixing increased the complexity of decoding the keys as well as thereby reducing instances of intrusions. However, similar WEP, WPA besides had a flaw. As such, WPA was advanced into WPA 2.
WPA2
WPA 2 is currently recognized equally the nearly secure protocol. Single nearly of import alter visible betwixt WPA as well as WPA2 is the mandatory role of AES (Advanced Encryption Standard) algorithms as well as the introduction of CCMP (Counter Cipher Mode amongst Block Chaining Message Authentication Code Protocol) equally a replacement for TKIP.
The CCM fashion combines Counter (CTR) fashion privacy as well as Cipher Block Chaining Message Authentication Code (CBC-MAC) authentication. These modes convey been extensively studied as well as are institute to convey well-understood cryptographic properties which render skilful safety as well as functioning inwards software or hardware.
Source: https://www.thewindowsclub.com/


comment 0 Comments
more_vert