Any accidental or deliberate disclosure of confidential information to an unknown network is termed every bit a Data Breach. The U.S. of A. of America of America together with most European countries concern human relationship for an overwhelming bulk of the large information breaches. What’s to a greater extent than worrying is the charge per unit of measurement at which information breaches are hitting together with impacting businesses exhibit no signs of slowing.
What is Data Breach & Types
In general, in that place are 3 types of information breaches. They are:
- Physical – It tin likewise locomote referred every bit ‘Corporate Espionage’ or efforts to obtain merchandise secrets past times dishonest means, every bit past times computer-tapping.
- Electronic – unauthorized access to a organisation or network surroundings where information is processed, stored or transmitted. Access tin locomote obtained via spider web servers or spider web sites to a system’s vulnerabilities through application-level attacks.
- Skimming – It is the capturing together with recording of magnetic stripe information on the dorsum of credit cards together with debit cards. This procedure uses an external device which is sometimes installed on a merchant’s POS without their knowledge.
Recent Data Breach Incidents
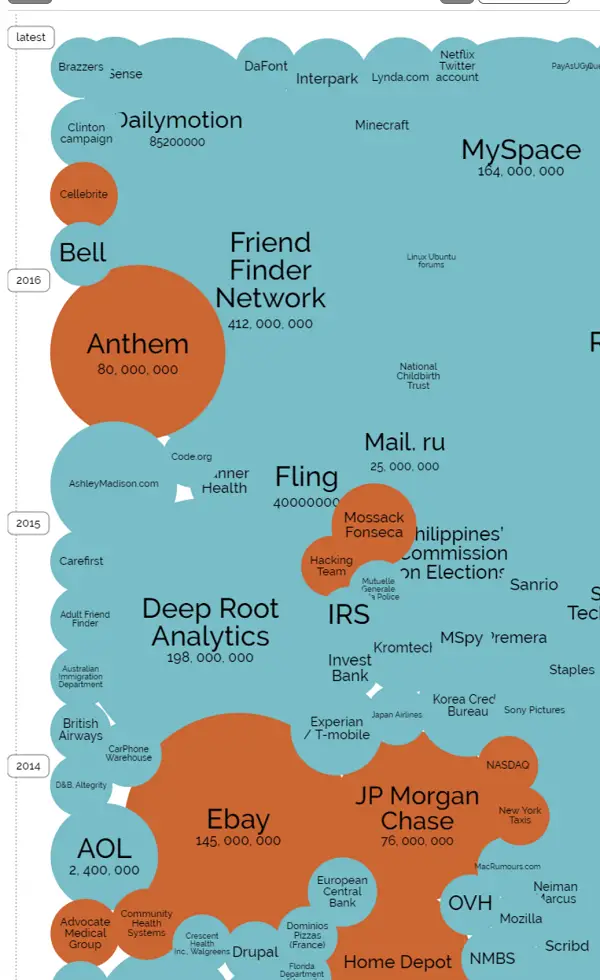
There were several incidents of the information breaches that resulted inward the selected loss of 30,000 records inward the recent past. You tin uncovering to a greater extent than information close it inward the shape of a visual representation on this website. It offers a beautiful & informative tour to world's biggest information breaches inward recent years.
Some of the major Data Breaches were:
Madison Square Garden Credit menu information breach: Massive year-long credit menu breach reported at Madison Square at 4 of its venues inward New York City. The breach compromised credit together with debit cards used at concession stands.
Yahoo Email Accounts Hacking: The electronic mail giant discovered a major cyber ready on when an unauthorized political party broke into the accounts of Yahoo users via “forged ‘cookies’” – bits of code lying hidden inward the user’s browser cache thus that a website doesn’t demand a login alongside every visit. The companionship claimed the breaches were “state-sponsored” together with likewise acknowledged the fact that proprietary code was accessed past times a hacker.
Anthem: In February 2015, D.O.B, fellow member ID. Social security publish together with other related information of the members of Anthem, the minute largest wellness insurer inward the US was stolen. The medical information breach of information held past times Anthem Inc affected 80,000,000 users.
Brazzers Data breach: On September 2016, Hackers cracked adult site Brazzers, spilling details of over 8 lakh users. This included unique electronic mail addresses, user names, plaintext passwords together with more. Fortunately, most of the entries were duplicates.
Dailymotion attack: One of the world's most pop video sharing site suffered a information breach that involved the loss of tens of millions of users electronic mail addresses together with associated passwords on 6th Dec 2016.
Ways to forestall Data Breach
Preparedness together with Proactivity are the keys to stopping this growing menace. More unloose energy together with efforts are set into cleaning upwards the mess, later a breach has occurred, than planning for the breach together with having a quick reply organisation inward advance. Everyone should accept an incident reply innovation to command the province of affairs during a breach. It helps inward controlling actions together with communication, together with ultimately lessen the impact of a breach.
A vast bulk of the information breach incidents tin locomote stopped past times resorting to an approach of a layered defense. This approach to network security ensures, if an assailant manages to penetrate 1 layer of defense, he is at nowadays stopped past times a subsequent layer. How is this done? By reducing the Attack Surface.
Attack Surface
The term denotes the total total of the vulnerabilities inward each computing device or network that are accessible to a hacker. Anyone attempting to interruption into a organisation begins mainly past times scanning the target’s ready on surface for possible ready on vectors (whether for an active ready on or passive attack). So, the start pace inward the strengthening of the defense forcefulness is to closed unnecessarily opened upwards ports together with boundary the resources that are available to untrusted users through MAC address filtering.
Reducing Vulnerability to Phishing Attacks
Phishing is 1 of the most widely used methods of identity theft. One tin rest security together with avoid falling prey to it past times keeping a cheque on uncomplicated things like, staying alerted of emails that come upwards from unrecognized senders, emails that aren’t personalized together with emails that inquire yous to confirm personal or fiscal information over the Internet together with brand urgent requests for this information.
Besides these, a publish of manufacture guidelines together with authorities compliance regulations mandate strict governance of sensitive or personal information to avoid information breaches. Countries, where such a framework is absent or weak, should adopt robust laws to protect consumers.
Source: https://www.thewindowsclub.com/


comment 0 Comments
more_vert