Honeypots are traps which are laid to abide by attempts at whatever unauthorized utilisation of information systems, amongst a thought to learning from the attacks to farther improve figurer security.
Traditionally, sustaining network safety has involved acting vigilantly, using network-based defence techniques similar firewalls, intrusion detection systems, together with encryption. But the electrical current province of affairs demands to a greater extent than proactive techniques to detect, deflect together with counteract attempts at illegal utilisation of information systems. In such scenario, the utilisation of honeypots is a proactive together with promising approach to struggle off network safety threats.
What is a Honeypot
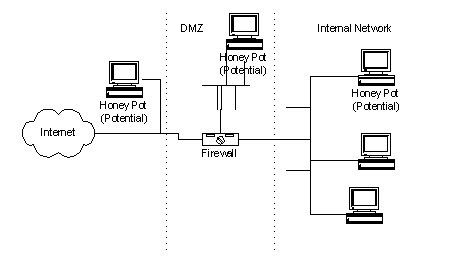
Considering the classical plain of figurer security, a figurer needs to live on secure, but inwards the domain of Honeypots, the safety holes are laid to opened upward on purpose. Honeypots tin bathroom live on defined every bit a trap which is laid to abide by attempts at whatever unauthorized utilisation of information systems. Honeypots essentially plough on the tables for Hackers together with figurer safety experts. The main role of a Honeypot is to abide by together with acquire from the attacks together with farther utilisation the information to improve security. Honeypots bring long been used to rail attackers' activity together with defend against coming threats. There are 2 types of honeypots:
- Research Honeypot – Influenza A virus subtype H5N1 Research Honeypot is used to written report virtually the tactics together with techniques of the intruders. It is used every bit a sentry post service to encounter how an assaulter is working when compromising a system.
- Production Honeypot – These are primarily used for detection together with to protect organizations. The main role of a production honeypot is to assist mitigate direct a opportunity inwards an organization.
Why fix Honeypots
The worth of a honeypot is weighed past times the information that tin bathroom live on obtained from it. Monitoring the information that enters together with leaves a honeypot lets the user assemble information that is non otherwise available. Generally, in that place are 2 pop reasons for setting upward a Honeypot:
- Gain Understanding
Understand how hackers probe together with drive to hit access to your systems. The overall thought is that since a tape of the culprit’s activities is kept, 1 tin bathroom hit agreement into the assault methodologies to ameliorate protect their existent production systems.
- Gather Information
Gather forensic information that is needed to assist inwards the apprehension or prosecution of hackers. This is the sort of information which is oft needed to furnish police enforcement officials amongst the details needed to prosecute.
How Honeypots secure Computer Systems
A Honeypot is a figurer connected to a network. These tin bathroom live on used to examine the vulnerabilities of the operating scheme or the network. Depending on the variety of setup, 1 tin bathroom written report safety holes inwards full general or inwards particular. These tin bathroom live on used to abide by activities of an private which gained access to the Honeypot.
Honeypots are by together with large based on a existent server, existent operating system, along amongst information that looks similar real. One of the primary differences is the place of the motorcar inwards relation to the actual servers. The most vital activity of a honeypot is to capture the data, the mightiness to log, alert, together with capture everything the intruder is doing. The gathered information tin bathroom examine to live on quite critical against the attacker.
High-Interaction vs. Low-Interaction Honeypots
High-interaction honeypots tin bathroom live on compromised entirely, permitting an enemy to hit total access to the scheme together with utilisation it to launch farther network attacks. With the assist such honeypots, users tin bathroom acquire to a greater extent than virtually targeted attacks against their systems or fifty-fifty virtually insider attacks.
In contrast, the low-interaction honeypots pose on only services which cannot live on exploited to become consummate access to the honeypot. These are to a greater extent than express but are useful for gathering information at a higher level.
Advantages of using Honeypots
- Collect Real Data
While Honeypots collect a small-scale book of information but almost all of this information is a existent assault or unauthorized activity.
- Reduced False Positive
With most detection technologies (IDS, IPS) a large fraction of alerts is faux warnings, spell amongst Honeypots this doesn’t check true.
- Cost Effective
Honeypot precisely interacts amongst malicious activity together with does non require high-performance resource.
- Encryption
With a honeypot, it doesn't affair if an assaulter is using encryption; the activity volition withal live on captured.
- Simple
Honeypots are real unproblematic to understand, deploy together with maintain.
A Honeypot is a concept together with non a tool which tin bathroom live on merely deployed. One needs to know good inwards advance what they intend to learn, together with and thence the honeypot tin bathroom live on customized based on their specific needs. There is around useful information on sans.org if yous demand to read to a greater extent than on the subject.
Source: https://www.thewindowsclub.com/


comment 0 Comments
more_vert