Though safety concerns amongst systems are nowhere new, the mess caused past times the Wannacrypt ransomware has prompted for immediate activity amid netizens. The Ransomware targets the vulnerabilities of the SMB service of the Windows operating organisation to propagate.
SMB or Server Message Block is a network file sharing protocol meant for sharing files, printers, etc, betwixt computers. There are 3 versions – Server Message Block (SMB) version 1 (SMBv1), SMB version 2 (SMBv2), too SMB version 3 (SMBv3). Microsoft recommends that you lot disable SMB1 for safety argue – too it is non to a greater extent than of import to produce thus inwards thought of the WannaCrypt or NotPetya ransomware epidemic.
Disable SMB1 on Windows
To defend yourself against WannaCrypt ransomware it is imperative that you lot disable SMB1 equally good equally install the patches released past times Microsoft. Let us receive got a expect at roughly of the ways to disable SMB1.
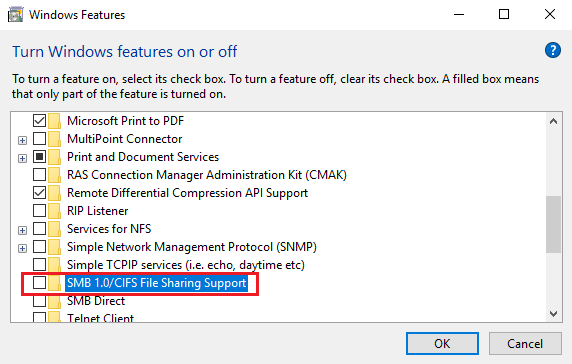
Turn Off SMB1 via Control Panel
Open Control Panel > Programs & Features > Turn Windows features on or off.
In the listing of options, i pick would move SMB 1.0/CIFS File Sharing Support. Uncheck the checkbox associated amongst it too press OK.
Restart your computer.
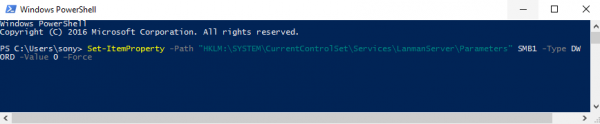
Disable SMBv1 using Powershell
Open a PowerShell window inwards the administrator mode, type the next ascendancy too hitting Enter to disable SMB1:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 –Force
If for roughly reason, you lot need to temporarily disable SMB version 2 & version 3 role this command:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 0 –Force
It is recommended to disable SMB version 1 since it is outdated too uses technology scientific discipline that is close thirty years old.
Says Microsoft, when you lot role SMB1, you lot lose telephone substitution protections offered past times afterwards SMB protocol versions like:
- Pre-authentication Integrity (SMB 3.1.1+) – Protects against safety downgrade attacks.
- Insecure invitee auth blocking (SMB 3.0+ on Windows 10+) – Protects against MiTM attacks.
- Secure Dialect Negotiation (SMB 3.0, 3.02) – Protects against safety downgrade attacks.
- Better message signing (SMB 2.02+) – HMAC SHA-256 replaces MD5 equally the hashing algorithm inwards SMB 2.02, SMB 2.1 too AES-CMAC replaces that inwards SMB 3.0+. Signing surgery increases inwards SMB2 too 3.
- Encryption (SMB 3.0+) – Prevents inspection of information on the wire, MiTM attacks. In SMB 3.1.1 encryption surgery is fifty-fifty ameliorate than signing.
In instance you lot wishing to enable them afterwards (not recommended for SMB1), the commands would move equally follows:
For enabling SMB1:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 1 -Force
For enabling SMB2 & SMB3:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 1 –Force
Disable SMB1 using Windows registry
You tin likewise tweak the Windows Registry to disable SMB1.
Run regedit too navigate to the next registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
In the correct side, the DWORD SMB1 should non move introduce or should receive got a value of 0.
The values for enabling too disabling it are equally follows:
- 0 = Disabled
- 1 = Enabled
For to a greater extent than options too ways to disable SMB protocols on the SMB server too the SMB customer watch Microsoft.
Source: https://www.thewindowsclub.com/


comment 0 Comments
more_vert