Protecting our information online is never going to last an slowly task, peculiarly nowadays when attackers are regularly inventing around novel techniques in addition to exploits to pocket your data. Sometimes their attacks will not last thus harmful for individual users. But large-scale attacks on around pop websites or fiscal databases could last highly dangerous. In near cases, the attackers outset motility to force around malware on to user’s machine. Sometimes this technique doesn't work out, however.
Image source: Kaspersky.
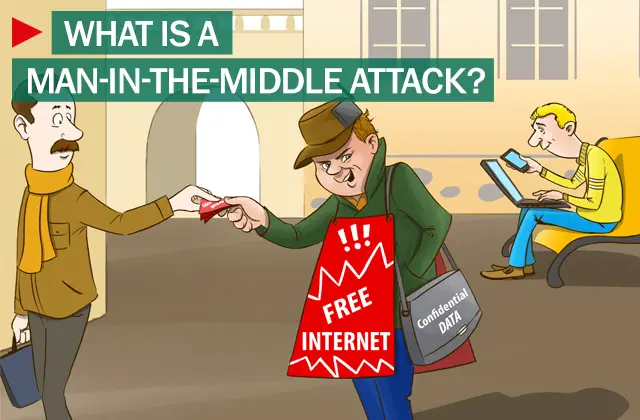
What is Man-In-The-Middle Attack
A pop method is Man-In-The-Middle attack. It is also known every bit a bucket brigade attack, or sometimes Janus attack in cryptography. As its get upward suggests, the assaulter keeps himself/herself betwixt 2 parties, making them believe that they are talking straight to each other over a private connection, when genuinely the entire conversation is beingness controlled yesteryear the attacker.
A man-in-the-middle assail tin last successful alone when the assaulter forms a mutual authentication betwixt 2 parties. Most cryptographic protocols ever supply around shape of endpoint authentication, specifically to block MITM attacks on users. Secure Sockets Layer (SSL) protocol is ever beingness used to authenticate ane or both parties using a mutually trusted certification authority.
How it works
Let's say at that topographic point are 3 characters inwards this story: Mike, Rob, in addition to Alex. Mike wants to communicate amongst Rob. Meanwhile, Alex (attacker) inhibit the conversation to eavesdrop in addition to comport on a fake conversation amongst Rob, behalf on Mike. First, Mike asks Rob for his populace key. If Rob provides his cardinal to Mike, Alex intercepts, in addition to this is how “man-in-the-middle attack” begins. Alex thus sends a forged message to Mike that claims to last from Rob but including Alex's populace key. Mike easily believes that the received cardinal does belong to Rob when that’s non true. Mike innocently encrypts his message amongst Alex’s cardinal in addition to sends the converted message dorsum to Rob.
In the near mutual MITM attacks, assaulter generally uses a WiFi router to intercept user's communication. This technique tin last run out yesteryear exploiting a router amongst around malicious programs to intercept user’s sessions on the router. Here, the assaulter outset configures his laptop every bit a WiFi hotspot, choosing a get upward unremarkably used inwards a populace area, such every bit an aerodrome or java shop. Once a user connects to that malicious router to arrive at websites such every bit online banking sites or commerce sites, the assaulter thus logs a user’s credentials for subsequently use.
Man-in-the-middle assail prevention & tools
Most of the effective defenses against MITM tin last found alone on router or server-side. You won't be having whatever dedicated command over the safety of your transaction. Instead, yous tin purpose rigid encryption betwixt the customer in addition to the server. In this case, server authenticates client's asking yesteryear presenting a digital certificate, in addition to thus the alone connexion could last established.
Another method to forbid such MITM attacks is, to never connect to opened upward WiFi routers directly. If yous wishing to so, yous tin use a browser plug-in such every bit HTTPS Everywhere or ForceTLS. These plug-ins volition assistance yous establishing a secure connexion whenever the selection is available.
TIP: Download this tool to speedily honour & cook Windows errors automatically


comment 0 Comments
more_vert