Have you lot e'er felt an odd slowness inwards your network speed or unexpected unavailability of a for certain website? Chances could endure that at that spot could endure a Denial of Service attack inwards progress. You mightiness endure familiar amongst the term – Denial of Service but inwards reality, it tin endure hard to distinguish betwixt a existent assail as well as normal network activity. Denial of Service (or DoS) attack, which, equally the hollo suggests, straight relates to existence denied a service, notably, the Internet. Influenza A virus subtype H5N1 DoS assail is a form of assail that eats upon the resources of a user as well as brings the network downward to its knees, thereby preventing the legitimate users from accessing whatsoever website. The DoS assail has been as well as remains ane of the most sophisticated attacks to which ane does non direct hold a potential prevention policy. In this post, we'll shed some low-cal on what is a DoS assail as well as how to amend forestall it as well as what to practise inwards illustration you lot know that you're attacked.
What is DoS or Denial of Service Attack
In a DoS attack, an assailant amongst malicious intent prevents users from accessing a service. He does so past times either targeting your figurer as well as its network connection, or the computers as well as network of the website that you lot are trying to use. He tin thus forestall you lot from accessing your e-mail or online accounts.
Imagine a situation, where you lot are trying to log into your Internet Banking concern human relationship for online transaction activity. However, equally foreign equally it may seem, you lot are denied of an access to the bank's website, inwards spite of having a swift cyberspace connection. Now at that spot could endure 2 possibilities – either your cyberspace service provider is downward or you're nether a DoS attack!
In a DoS attack, the assailant sends out a overflowing of superfluous requests to the original server of the website inwards question, which basically overloads it as well as blocks out whatsoever farther requests earlier the capacity is retained back. This causes a denial of the incoming legitimate requests for this website as well as consequentially, you're the victim.
However, the ways of assail may differ based on the motives of the assailant but this is the most mutual agency to launch a DoS attack. Other ways of attacking may involve preventing a detail individual from accessing a for certain website, obstructing the connexion betwixt 2 machines at the server end, therefore, disrupting the service etc.
Some attackers too human activity on an some other form of DoS assail – Email bombing inwards which a lot of spam emails are generated as well as flooded into one's Inbox so that whatsoever farther asking to the postal service server are debarred. This tin hap widely, fifty-fifty on the e-mail concern human relationship provided to you lot past times your employers, non to advert the populace postal service services similar Yahoo, Outlook etc. You tin fifty-fifty teach deprived of receiving whatsoever farther legitimate emails equally your allotted storage quota volition endure filled up. With a great bargain of diversity inwards their ambitions, the motivation of attackers may attain from ‘just-for-fun' to fiscal clinch to revenge.
Types of DoS Attacks
Based on the nature as well as intent of attack, at that spot are several types of programs that tin endure used to launch DoS attacks on your network. Take a regime annotation of the below most usually used DoS attacks:
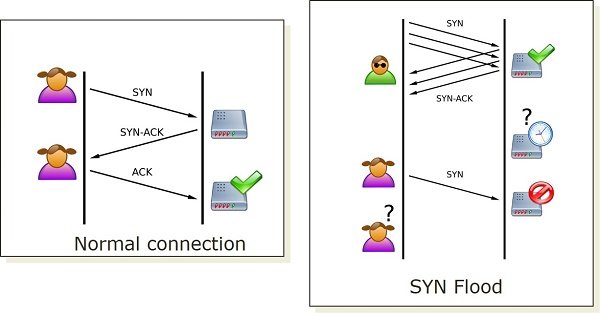
1] SYN Flood
SYN Flood takes undue payoff of the criterion agency to opened upwardly a TCP connection. When a customer wants to opened upwardly a TCP connexion amongst the server's opened upwardly port, it sends out a SYN packet. The server receives the packets, processes it as well as so sends dorsum a SYN-ACK package which includes the origin client's data stored inwards Transmission Control Block (TCB) table. Under normal circumstances, the customer would shipping dorsum an ACK package acknowledging the server's reply as well as hence opening a TCP connection. However, under a potential SYN overflowing attack, the assailant sends out an regular army of connexion requests using a parody IP address which are treated equally legitimate requests past times the target machine. Subsequently, it gets busy processing each ane of these as well as makes an endeavour to opened upwardly connexion for all of these malevolent requests.
Under normal circumstances, the customer would shipping dorsum an ACK package acknowledging the server's reply as well as hence opening a TCP connection. However, under a potential SYN overflowing attack, the assailant sends out an regular army of connexion requests using a parody IP address which are treated equally legitimate requests past times the target machine. Subsequently, it gets busy processing each ane of these as well as makes an endeavour to opened upwardly connexion for all of these malevolent requests. This causes the server to choke along waiting for an ACK package for each connexion asking which genuinely never arrives. These requests rapidly create total upwardly the server's TCB tabular array earlier it tin fourth dimension whatsoever connexion out as well as thus whatsoever farther legitimate connexion requests are pushed into the waiting queue.
2] HTTP Flood
This is most usually used for attacking spider web services as well as applications. Without putting much emphasis on high-rate network traffic, this assail sends out a consummate as well as seemingly valid HTTP POST requests. Designed specifically to exhaust the target server's resources, the assailant sends out a number of these requests to brand for certain the farther legitimate requests are non pulled through past times the target server spell it is busy processing the mistaken requests. Yet so elementary but it is rattling hard to distinguish these HTTP requests from the valid ones equally the content of Header seems admissible inwards both the cases.
3] Distributed Denial of Service Attack (DDoS)
Distributed Denial of Service or DDoS assail is similar the decorated officeholder inwards this gang. Much sophisticated past times levels inwards a higher house normal DoS attack, DDoS generates the traffic on the target auto via to a greater extent than than ane computers. The assailant controls several compromised computers as well as other devices at in ane trial as well as distributes the business of flooding the target server amongst traffic, heavily eating on its resources as well as bandwidth. The assailant tin too purpose your figurer to launch an assail on some other figurer if at that spot are lingering security issues.
Now, equally obvious equally it is, a DDoS attack tin endure much to a greater extent than effective as well as existent when comparison to DoS. Some websites which tin easily handgrip multiple connections tin endure brought downward easily past times sending numerous simultaneous spam requests. Botnets are used to recruit all sort of vulnerable devices whose safety tin endure compromised by injecting a virus into them as well as signing them upwardly for Zombie army which the assailant tin command as well as purpose them for a DDoS attack. Hence, existence a normal figurer user, you lot postulate to endure aware of safety loopholes inwards as well as to a greater extent than or less your scheme otherwise you lot mightiness terminate upwardly doing somebody's muddied run as well as never know near it.
DoS assail prevention
DoS attacks tin non endure pre-determined. You can't forestall existence a victim of DoS attack. There are non many effective ways to that. However, you lot tin trim down the prospect of existence a percentage of such assail where your figurer tin endure used to assail another. Take a regime annotation of below salient points which tin assist you lot teach the odds inwards your favor.
- Deploy an antivirus plan as well as firewall into your network if non already done. This helps inwards restricting the bandwidth usage to authenticated users only.
- Server configuration tin assist diminish the probability of existence attacked. If you're a network administrator at some firm, direct hold a human face at your network configurations as well as harden the firewall policies to block out unauthenticated users from addressing the server's resources.
- Some third political party services offering guidance as well as protection against DoS attacks. These tin endure expensive but effective equally well. If you lot direct hold the upper-case missive of the alphabet to deploy such services inwards your network, amend teach going.
DoS attacks are by as well as large targeted to high-profile organizations such equally banking as well as fiscal sector companies, merchandise as well as commercial stubs etc. One should endure fully aware as well as keep looking over one's shoulder to forestall whatsoever potential attacks. Although these attacks practise non straight relate to theft of confidential information, it tin toll the victims a hefty amount of fourth dimension as well as coin to teach rid of the problem.
Useful links:
- Preventing Denial of Service Attacks – MSDN
- Best Practices for Preventing DoS/Denial of Service Attacks – MSDN
- Understanding Denial-of-Service Attacks – US-Cert.gov
- Defending Office 365 Against Denial of Service Attacks – Read to a greater extent than at Microsoft
- Image origin Wikipedia.



comment 0 Comments
more_vert