The Internet is definitely non a secure house for exchanging information. There are many prying eyes on yous trying to larn a slice of your hugger-mugger information. In this era of free-flowing data; most of us utilization the Internet connector in addition to have got access to information from all across the basis at our fingertips. And the Tor Network plant perfectly here, every bit it routes the user’s system’s Internet traffic over several places on the Internet. Thus, it hides the existent root of the communication in addition to secures user’s personal identity. Here is a detailed analysis of Tor or The Onion Router network and how it is used.
Tor Network
- What is Tor?
TOR or the Onion Router is a costless software in addition to opened upwards network which allows users to amend their privacy in addition to safety over the Internet. Putting inwards elementary words, Tor is software that allows the users to browse the Web anonymously.
- Who Developed It?
The Tor Project has developed Tor Network. This is a non-profit organisation which conducts query in addition to evolution on the online privacy in addition to obscurity.
- Why Was It Designed?
TOR is typically designed to halt people (including the authorities agencies in addition to corporations) to runway a user’s identity, location or browsing habits.
- Why Was It Called Onion Router?
Originally Tor was called The Onion Router; this is because this software uses a technique known every bit onion routing to conceal information close user activity.
- Is Tor Used For Browsing The Web Only?
The Tor network entails of Tor relays which road traffic. It is precisely non used for spider web browsing but tin also last used past times many applications which desire to anonymously road traffic. Applications similar Instant Messaging (IM), Internet Relay Chat (IRC) in addition to spider web browsers all tin utilization Tor effectively to anonymously road traffic across the Internet.
How does Tor work
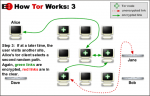
Tor routes the meshing traffic through the Tor Network. We already mentioned before that Tor could last used past times a pose out of applications, but hither let’s have got the spider web browser every bit an representative to explicate how Tor works.
- When a user tries to connect to a server using Tor, their browser launches an encrypted link amongst a Tor server. Further, it establishes a circuit or a path through the Tor network. This really path routes the traffic through several Tor servers. Note this path is random in addition to changes every 10 minutes.
- Once the path is established through the network, the packets are routed from i server to the other. On the network chain, whatever given server knows alone the server from where it has received the information in addition to the side past times side server to post that really data. None of the servers inwards this chain would genuinely know the entire path of the traffic that it takes through the network. This means Tor prevents inwards disclosing where the traffic came from in addition to where it is going to.
- Tor encrypts the traffic using a layering scheme; this is where the Onion concept comes from. For instance, every bit the traffic passes through the nodes inwards the Tor network, a layer of encryption is stripped off at each of the nodes, this looks similar layers of an onion.
- While using the Tor browser, the traffic is encrypted betwixt the browser in addition to the Tor network. It is sent anonymously through the network in addition to the finally node or the “exit node” uses an “Unencrypted” link to communicate amongst the goal server exterior the Tor network. Note that this concluding hop is non encrypted.
Who tin utilization Tor network in addition to for what purpose
Many people believe that their identity is properly protected nether normal usage conditions. But that is a totally incorrect concept every bit if yous are non using a VPN software or Tor, in that location is a high peril for your identity to last traced. Tor tin help users brand certain that their entire online action in addition to personal information stays secret.
Typically Tor Network is beingness used to:
- Keep meshing activities private from websites in addition to advertisers
- Answer cyber-spying concerns
- Evade hostile authorities censorship
- Avoid surveillance
- Ensure maximum privacy over the Internet
The U.S. of A. Navy is a cardinal user of the Tor Network. The primary audience for Tor include the journalists, legal activists, whistle-blowers, in addition to people living inwards a province amongst censorship. Other cardinal users include bloggers, work organisation executives, information technology professionals in addition to law enforcement officers. Also, the constabulary is a user of Tor, they utilization this network when they demand to mask their IP addresses patch investigating doubtful websites in addition to services.
Despite the skillful intentions of the Tor Project, Tor has unfortunately developed a bad reputation inwards the mainstream press. With the increase in addition to prosperity of Tor in addition to the massive payoff of the embrace it provides, the Tor Network has genuinely move a shelter for nasty individuals.
How to larn Tor
Tor is costless to utilization software; yous tin precisely download in addition to install the Tor browser. It is a modified version of Firefox which is available for Windows, Mac OS X, in addition to Linux. For mobile browsing, Orbot is an Android app available to download from Google Play.
Using Privoxy And Tor For Increased Anonymity
Tor Network has unopen to major disadvantages:
- Long plenty session
- Slow performance
- All the requests come upwards through i node.
To conclude inwards elementary words, the Tor Network tin last painfully slow. This is i major argue why nosotros advise using Privoxy amongst Tor.
What is Privoxy
Privoxy is a non-caching spider web proxy amongst advanced filtering capabilities. It is used for enhancing privacy, modifying spider web page information in addition to HTTP headers, command access, in addition to take away ads in addition to other obnoxious Internet junk. Privoxy in addition to Tor together brand a groovy team. They add together 2 additional layers of protection on your anonymous VPN.
Tor is a perfect tool to protect your digital privacy, fifty-fifty patch browsing the Internet without revealing who yous genuinely are!
Now read close the OONI or Open Observatory of Network Interference Project from TOR.
Source: https://www.thewindowsclub.com/




comment 0 Comments
more_vert