In this era of technology, at that topographic point are many proficient people trying to do first-class networks to help people similar us to communicate, function alongside others in addition to larn information. On the other hand, at that topographic point are exactly about not-so-good people who for a multifariousness of reasons, tend to role their computers in addition to brand means into the networks in addition to motility problem to others. Yes, they are the Hackers. These hackers are ever at work.
Yesterday, nosotros took a hold back at the signs of a hacked estimator in addition to what to do if your estimator has been hacked. The adjacent inquiry to come upwards to one's heed is Why would someone desire to hack my computer? Let’s essay in addition to uncovering the response to this inquiry inwards detail.
Hacking is the procedure past times which a hacker attempts to gain unauthorized access to estimator resources alongside malicious intent. So, basically, a hacker wants to run into in addition to role the information on your estimator or mayhap role your estimator to demeanor out online attacks on others. Hackers appear to conduct hold considered exploiting networks to hold upwards their personal mission ever since the networked computers were invented. Now, since at that topographic point is a possibility of connecting all devices alongside each other; including the ones inwards our pockets, or the ones on our vehicle; the conduct chances of information safety breach is much greater than ever before.Hacking is on the rise, in addition to instantly it is much easier for the hackers to access our files without our fifty-fifty knowing most it.
There are several forms of Cyber Attacks used against computers in addition to networks – from malware injection to phishing to social applied scientific discipline to the internal stealing of data. Other advanced but mutual forms are DDoS Attacks, Brute Force attacks, hacking, belongings a estimator arrangement (or a website) for ransom using straight hack or Ransomware.
Why would someone desire to hack my computer
When nosotros cry back of hacking, nosotros ever cry back it’s the sensitive information existence stolen in addition to used for exactly about fiscal gain. But this does non appear to hold upwards the solely argue why would someone desire to hack my computer.
These are the reasons why someone would desire to hack your computer:
- To role it every bit a Internet Relay Chat (IRC) server, for Storage or for DDoS Attacks.
- Criminal & Financial gain
- Industrial espionage
- Make it a business office of a Botnet
- For fun & excitement.
Let us conduct hold a hold back at exactly about of these.
1. To role our computer:
Hackers tin hack our estimator to role it for the next reasons-
- Internet Relay Chat (IRC) server: Hackers tin role our PC every bit an IRC Server. This is because they don’t desire to verbalise over their activities openly on their ‘own’ servers.
- Storage: Hackers mightiness desire to role our PC every bit a storage device for their unlawful materials. Pirated software, pirated music, pornography in addition to hacking tools are exactly about examples of the unlawful materials.
- DDoS Attack: Our PC tin hold upwards used every bit a business office of a DDoS attack. The hackers command many computers inwards an endeavour to motility resources starvation on a victim’s computer.
2. Criminal gain:
There are exactly about hackers who role their hacking skills to shape criminal activities. Here, the hackers mightiness hack the estimator to steal services of the user in addition to also their valuable files in addition to information. This tin hold upwards done on:
- Personal level: On a personal level, hackers assault personal computers to larn access to passwords in addition to fiscal information. They tin role such information to defraud the individual.
- Larger level: Groups of hackers tin target companies every bit a business office of a much wider criminal operation.
3. Financial gain:
Hackers oft deed for fiscal gain. They tin do this either individually or inwards coordinated groups. Many professional person criminals role hacking to brand coin past times using hacking techniques. They do this too:
- Set upwards a imitation e-commerce site to collect credit bill of fare details
- Gain entry to the servers which comprise credit bill of fare details
- Engage inwards dissimilar forms of credit bill of fare fraud
- Install Ransomware.
4. Hack for fun, thrill, in addition to excitement:
Some hackers essay to hack a arrangement to crevice a challenge. They exactly hack our computers to essay out the skills they conduct hold in addition to breach the systems. They are non actually the ones interested inwards doing anything malicious when they are inwards control.
5. Other reasons
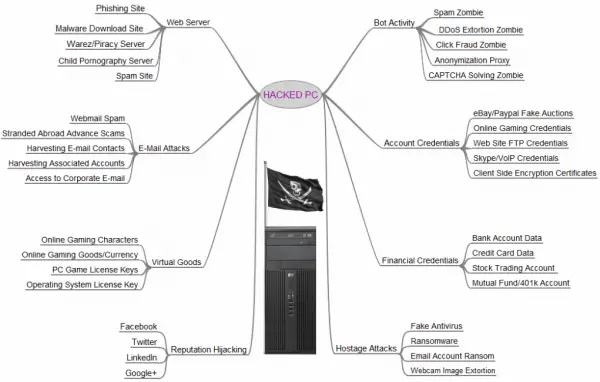
Apart from these reasons, I constitute several other reasons why someone desire to hack your estimator at this first-class infographic from krebsonsecurity.com. You may click on the Infographic to stance it inwards the larger size.
Computer breaches getting harder to prevent
While trying to uncovering reasons behind why would someone desire to hack my computer, I also constitute that estimator breaches conduct hold cash inwards one's chips much easier to execute. Unfortunately, it is much harder to preclude for several reasons:
- Extensive role of Internet in addition to network connectivity
- Secrecy provided past times estimator systems working over the Internet
- Large in addition to growing numbers of hacking tools available openly
- More in addition to to a greater extent than opened upwards wireless networks
- Tech in addition to computer-savvy children
- Unlikeliness of existence caught
Anyone connecting to the Internet is susceptible to existence hacked. Also, regardless of the motivation, hacking is a serious conduct chances to personal in addition to national security.
To rest safe, cash inwards one's chips along your operating arrangement in addition to installed software updated at all times in addition to thus every bit to unopen all software vulnerabilities, role a proficient security software in addition to follow safe computing best practices in addition to full general Internet Security tips. Here are exactly about more tips that volition help you lot cash inwards one's chips along Hackers out of your Windows computer.
Source: https://www.thewindowsclub.com/



comment 0 Comments
more_vert