In an before post, nosotros stimulate got seen how to bypass login hide inwards Windows 7 as well as older versions past times taking wages of AutoLogon tool offered past times Microsoft. It was also mentioned that major produce goodness of using AutoLogon tool is that your password is non stored inwards plain text form equally is done when y'all manually add together the registry entries. It is start encrypted as well as thence stored thence that fifty-fifty the PC Administrator does non stimulate got access to the same. In today's post, we'll utter close how to decrypt the DefaultPassword value saved inwards Registry editor past times using AutoLogon tool.
First things first, you'd notwithstanding need to have Administrator privileges inwards monastic say to decrypt the DefaultPassword value. The argue behind this obvious restriction is that such encrypted system as well as user information are governed past times a particular safety policy, knows equally Local Security Authority (LSA) which grants the access solely to the organisation administrator. So, before nosotros brand our motion on decrypting the passwords, let's accept a await at this safety policy and it's co-related know-hows.
LSA – What it is as well as how it stores data
LSA is used past times Windows to create out the system's local safety policy as well as perform the auditing as well as authentication procedure on the users logging into the organisation acre saving their somebody information to a particular storage location. This storage place is called LSA Secrets where of import information used past times LSA policy is saved as well as protected. This information is stored inwards an encrypted cast inwards the registry editor, inwards the HKEY_LOCAL_MACHINE/ Security/ Policy/ Secrets key, which is non visible to full general user accounts due to restricted Access Control Lists (ACL). If y'all stimulate got the local administrative privileges as well as know your agency closed to LSA Secrets, y'all tin larn access to the RAS/VPN passwords, Autologon passwords, as well as other organisation passwords/keys. Below is a listing to name a few.
- $MACHINE.ACC: Related to Domain Authentication
- DefaultPassword: Encrypted password value if AutoLogon is enabled
- NL$KM: Secret primal used to encrypt cached domain passwords
- L$RTMTIMEBOMB: To shop the final engagement value for Windows activation
In monastic say to create or edit the secrets, at that spot is a particular prepare of APIs available for software developers. Any application tin larn access to the LSA Secrets place but solely inwards the context of the current user account.
How to decrypt the AutoLogon password
Now, inwards monastic say to decrypt and uproot the DefaultPassword value stored inwards LSA Secrets, 1 tin merely termination a Win32 API call. There is a unproblematic executable plan available for getting the decrypted value of DefaultPassword value. Follow the below steps to produce so:
- Download the executable file from here – it's precisely ii KB inwards size.
- Extract the contents of DeAutoLogon.zip file.
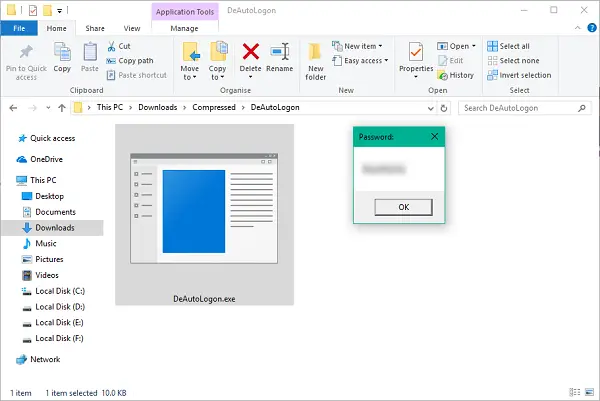
- Right-click DeAutoLogon.exe file as well as run it equally Administrator.
- If y'all stimulate got the AutoLogon characteristic enabled, DefaultPassword value should live on correct at that spot inwards front end of you.
If y'all endeavor to run the plan without Administrator privileges, you'd run across an error. Hence, brand certain to larn local administrator privileges before running the tool. Hope this helps!
Shout out inwards the comments department below inwards illustration you've got whatever question.
Source: https://www.thewindowsclub.com/


comment 0 Comments
more_vert