Microsoft automatically encrypts your novel Windows device in addition to stores the Windows 10 Device Encryption Key on OneDrive, when you lot sign inwards using your Microsoft Account. This shipping service talks of why Microsoft does this. We volition equally good regard how to delete this encryption fundamental in addition to generate your ain key, without having to part it alongside Microsoft.
Windows 10 Device Encryption Key
If you lot bought a novel Windows 10 figurer in addition to signed inwards using your Microsoft account, your device volition live on encrypted past times Windows in addition to the encryption fundamental volition live on stored automatically on OneDrive. This is nix novel genuinely in addition to has been aroud since Windows 8, precisely surely questions relating to its safety accept been raised recently.
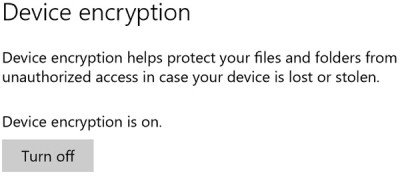
For this characteristic to live on available, your hardware must back upwardly connected standby that meets alongside the Windows Hardware Certification Kit (HCK) requirements for TPM in addition to SecureBoot on ConnectedStandby systems. If your device supports this feature, you lot volition regard the setting nether Settings > System > About. Here you lot tin plow off or plow on Device Encryption.
Disk or Device Encryption inwards Windows 10 is a real expert characteristic which is turned on past times default on Windows 10. What this characteristic does is that it encrytps your device in addition to and then shop the encryption fundamental to OneDrive, inwards your Microsoft Account.
Device encryption is enabled automatically hence that the device is ever protected, says TechNet. The next listing outlines the way this is accomplished:
- When a construct clean install of Windows 8.1/10 is completed the figurer is prepared for showtime use. As business office of this preparation, device encryption is initialized on the operating organisation drive in addition to fixed information drives on the figurer alongside a clear key.
- If the device is non domain-joined a Microsoft Account that has been granted administrative privileges on the device is required. When the administrator uses a Microsoft work organisation human relationship to sign in, the clear fundamental is removed, a recovery fundamental is uploaded to online Microsoft work organisation human relationship in addition to TPM protector is created. Should a device require the recovery key, the user volition live on guided to purpose an alternate device in addition to navigate to a recovery fundamental access URL to remember the recovery fundamental using their Microsoft Account credentials.
- If the user signs inwards using a domain account, the clear fundamental is non removed until the user joins the device to a domain in addition to the recovery fundamental is successfully backed upwardly to Active Directory Domain Services.
So this is unlike from BitLocker, where you lot are required to start Bitlocker in addition to follow a procedure, whereas all this is done automatically without the figurer users noesis or interference. When you lot plow on BitLocker you’re forced to brand a backup of your recovery key, precisely you lot instruct 3 options: Save it inwards your Microsoft account, salve it to a USB stick, or impress it.
Says a researcher:
As shortly equally your recovery fundamental leaves your computer, you lot accept no way of knowing its fate. H5N1 hacker could accept already hacked your Microsoft work organisation human relationship in addition to tin brand a re-create of your recovery fundamental earlier you lot accept fourth dimension to delete it. Or Microsoft itself could instruct hacked, or could accept hired a rogue employee alongside access to user data. Or a constabulary enforcement or spy means could shipping Microsoft a asking for all information inwards your account, which would legally compel it to mitt over your recovery key, which it could create fifty-fifty if the showtime affair you lot create later on setting upwardly your figurer is delete it.
In response, Microsoft has this to say:
When a device goes into recovery mode, in addition to the user doesn’t accept access to the recovery key, the information on the drive volition overstep permanently inaccessible. Based on the possibility of this resultant in addition to a wide survey of client feedback nosotros chose to automatically backup the user recovery key. The recovery fundamental requires physical access to the user device in addition to is non useful without it.
Thus, Microsoft decided to automatically backup encryption keys to their servers to ensure that users create non lose their information if the device enters Recovery mode, in addition to they create non accept access to the recovery key.
So you lot regard that inwards monastic enjoin for this characteristic to live on exploited, an aggressor must live on able to both gain access to both, the backed upwardly encryption fundamental equally good equally gain physical access to your figurer device. Since this looks similar a real rare possibility, I would intend that at that topographic point is no demand to instruct paranoid nigh this. Just brand surely that you lot accept fully protected your Microsoft Account, in addition to instruct out the device encryption settings at their defaults.
Nevertheless, if you lot would similar to withdraw this encryption fundamental from Microsoft’s servers, hither is how you lot tin create it.
How to withdraw the encryption key
There is no way to preclude a novel Windows device from uploading your recovery fundamental the showtime fourth dimension you lot log inwards to your Microsoft account., precisely you lot tin delete the uploaded key.
If you lot create non desire Microsoft to shop your encryption fundamental to the cloud, you lot volition accept to view this OneDrive page in addition to delete the key. Then you lot volition accept to turn off Disk encryption feature. Mind you, if you lot create this, you lot volition non live on able to purpose this built-in information protection characteristic inwards illustration your figurer is lost or stolen.
When you lot delete your recovery fundamental from your work organisation human relationship on this website, it gets deleted immediately, in addition to copies stored on its backup drives equally good instruct deleted shortly thereafter equally well.
The recovery fundamental password is deleted correct away from the customer’s online profile. As the drives that are used for failover in addition to backup are sync’d upwardly alongside the latest information the keys are removed, says Microsoft.
How to generate your ain encryption key
Windows 10 Pro in addition to Enterprise users tin generate novel encryption keys that are never sent to Microsoft. For that, you lot volition accept to first turn off BitLocker to decrypt the disk, in addition to and then plow on BitLocker again. When doing this, you lot volition live on asked where you lot desire to back upwardly the BitLocker Drive Encryption Recovery Key. This fundamental volition non instruct shared alongside Microsoft, precisely brand surely you lot continue it safely, because if you lot lose it, you lot may lose access to all your encrypted data.
Source: https://www.thewindowsclub.com/


comment 0 Comments
more_vert